As public-facing networks increasingly adopt open-source software, the transformation brings both innovation and complexity. While openness fosters flexibility and collaboration, it also introduces new challenges—especially in securing applications deployed across these networks. Safeguarding such dynamic environments is no easy feat.
A recent paper published on arXiv.org explores this very issue, focusing on the evolving security landscape in the era of 6G, which is being rapidly shaped by the Open Radio Access Network (O-RAN) paradigm. As O-RAN expands, so does the attack surface, making robust, intelligent threat mitigation more critical than ever.
Currently, most O-RAN applications emphasize network optimization and passive threat detection. However, they lack the capability for closed-loop, automated responses—an essential feature for real-time threat mitigation in next-gen networks.
To address this gap, researchers have proposed an innovative framework: MobiLLM—a multi-agent AI system designed for Closed-Loop Threat Mitigation in 6G Open RANs.
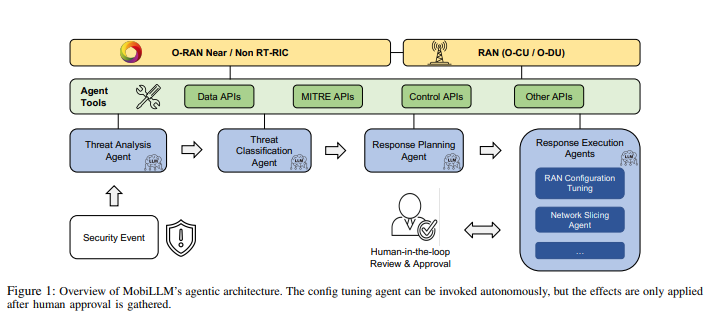
Introducing MobiLLM: Modular, Intelligent, and Safe
MobiLLM is built as a set of modular rApps and xApps within the O-RAN Service Management and Orchestration (SMO) framework. It integrates seamlessly using standard interfaces like O1 and A1, and is powered by Large Language Models (LLMs). The framework breaks down threat handling into three key stages:
- Threat Analysis Agent: Filters incoming data to identify genuine threats, distinguishing signal from noise.
- Threat Classification Agent: It uses Retrieval-Augmented Generation (RAG) and the MITRE FiGHT framework to map threats to known attack patterns with precision.
- Response Planning & Execution Agents: Translates mitigation strategies into safe, vetted actions to neutralize threats.
What sets MobiLLM apart is its emphasis on safety and reliability. It incorporates guardrails such as: Knowledge grounding, Schema enforcement and Human-in-the-loop approval
These features ensure that AI-driven actions remain secure and trustworthy—no rogue decisions, just intelligent automation.
Real-World Testing: Promising Results with Room to Grow
The researchers tested MobiLLM against five real-world 5G/6G attack scenarios, including: Denial-of-Service (DoS), IMSI exposure and Null cipher exploits.
Key outcomes were:
- Threat Classification Accuracy: 94% — a strong performance in identifying threats.
- Execution Success Rate: 64% — while effective in some cases (e.g., Null Cipher mitigation), it struggled with others like Downlink IMSI extraction.
These results highlight a limitation: general-purpose LLMs, though powerful, aren’t fully optimized for telecom-specific tasks.
The paper suggests that domain-specific, fine-tuned models could significantly enhance performance in handling advanced protocols.
Why This Matters for the Future of Telecom
MobiLLM represents a major leap forward in telecom security. By shifting from passive detection to automated, closed-loop responses, it reduces response times, cuts operational costs and additionally enhances network resilience.
In mission-critical 6G applications—such as smart cities, autonomous vehicles, and global communications—this kind of adaptive, intelligent defense is not just beneficial, it’s essential.
Moreover, the research offers a blueprint for trustworthy AI in network security, emphasizing the importance of human oversight and safety mechanisms in deploying autonomous systems.
Looking Ahead: The Road to Secure 6G
While MobiLLM is a promising start, the journey toward fully secure 6G networks continues. Future developments may include specialized telecom models, faster and more accurate response mechanisms, and deeper integration with O-RAN systems.
For now, MobiLLM proves that AI can do more than detect threats—it can fight back, intelligently and safely.
MobiLLM is a thrilling leap toward intelligent, adaptive telecom defenses. As 6G rolls out, could this be the key to making networks truly secure? What’s your take on AI handling live network threats—game-changer or too risky without more human oversight? Drop your thoughts below!
Be First to Comment